Monthly Shaarli
August, 2021
Based on facts and assumptions, this article summarizes how Apple's proprietary videotelephony protocol might work.

This post introduces Route Origin Authorization (ROA) and the implication of its usage for Twitter.
In this post, the author gives a short introduction to modern email domain security concepts.
Debian Pure Blends are a solution for groups of people with specific needs.
Blog post on why there is no such thing as a "root cause" in the context of complex systems failure.
Colin Percival compares boot times of different operating systems on EC2 with his tool ec2-boot-bench.
In this video, the speaker gives a practical introduction to SSH tunnels with lots of examples and configuration tips.
This post explains how attackers can abuse middleboxes and censorship infrastructure for DoS amplification attacks over TCP.

Suggests for improving Linux Kernel security, e.g. by converting redundant downstream kernel bug-fixing by vendors into greater upstream collaboration.
»If you like the interface of HTTPie but miss the features of curl, curlie is what you are searching for.«
Version 2021.07 of the Debian-based live system, primarily targeted at system administrators, was released.
An empirical study of vulnerabilities in cryptographic libraries.

In this article, Gareth Corfield comments on ENISA's supply chain attack report.
Even a laptop following security best practices does not keep attackers from exploiting it. In this case, a TPM secured, FDE SSD was targeted.
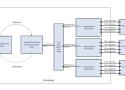
This post shows how HTTP/2 solved bottlenecks between frontend and storage nodes in LinkedIn's distributed object-store.
»A survey commissioned by industrial giant Honeywell showed that roughly a quarter of facility managers have admitted suffering a breach of operational technology (OT) systems in the past year.«
The PAM Duress is a module designed to allow users to generate 'duress' passwords that will execute arbitrary scripts when used in place of their regular password.

This article covers new features of the SystemTap version that will be available in RHEL 9.

»Hamburg's state government has been formally warned against using Zoom over data protection concerns.«
Debian 11 is out, some of the changes: systemd now defaults to using cgroupv2, the systemd journal is now persisted by default. Debian 11 includes over 11294 new packages, and the maintainers updated most of the existing ones. Version numbers of some well-known packages:
- PostgreSQL 13
- Samba 4.13
- Vim 8.2
- OpenSSH 8.4p1
- Nginx 1.18
- KDE Plasma 5.20

Facebook, Google, Isovalent, Microsoft, and Netflix launch eBPF Foundation as Part of the Linux Foundation.

This blog post introduces Facebook's Open Compute Time Appliance, based on the PCIe Time Card.
Timeline containing over 830 operating systems.

OpenShift 4.8 brings, among other improvements, an additional OCI-compliant runtime based on Kata Containers, NVIDIA multi-instance GPU, OpenShift Pipelines, IPv6 support, and serverless functions as a technology preview.
Paper about the cryptography and security analysis behind the Apple PSI system.
List of personal blogs focusing on software.
Amongst other news, the report for Q2 contains information on:
- A new, web-based installer.
- LLDB Debugger Improvements.
- Update of the Linux compatibility layer.
pfsyncookie support.- The RAIDZ expansion update
- helloSystem

This article summarizes the information on the upcoming z/OS 2.5 release.

In this post, the author shows that even if not always the most efficient solution, there still are use-cases where human-readable protocols shine.
The author explains why high-percentile latency is not a good way to measure efficiency.
»Suffice it to say, if you work someplace with enough machines, there's probably some way for you to get root on all of them if you can hit them with a handful of packets. I've seen it happen far too many times at enough companies to expect things to stay secure. I'm not talking about buffer overflows and stuff like that, although those exist too. I mean just straight up asking a service to please run a command for you (as root), and it gladly complies.«

»WinFsp is a set of software components for Windows computers that allows the creation of user mode file systems. In this sense it is similar to FUSE (Filesystem in Userspace), which provides the same functionality on UNIX-like computers.«
Besides other improvements and bug fixes, this release adds SFTP support for SCP as an eventual replacement to the SCP/RCP protocol and stricter configuration file parser for ssh and sshd.
The Haiku Project, originally named OpenBeOS, was founded in August 2001.
OSADL (Open Source Automation Development Lab): Open Source Software for Automation and Other Industries.

observatory-cli is the command-line version of Mozilla's Observatory, »a project designed to help developers, system administrators, and security professionals configure their sites safely and securely.«
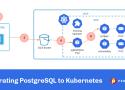
Blog post on migrating on-prem Postgres to a GKE cluster with Percona Operator.

Glowworm Attack: recovering sound by analyzing optical emanations from a device's power indicator LED.

This post explains the rationale behind the decision to switch from Debian to Arch Linux for SteamOS 3.0.
The Windows kernel native port of WireGuard was announced.
Cockpit 250 comes with basic kpatch support, an improved admin switcher, and VM migration.
Some of the new features are support for Java 11, Virtual Tables, Audit logging, and full query logging.

This blog post investigates HTTP/2 implementation issues and some of the resulting security implications.
Kubernetes hardening guide by the NSA and CISA.

This blog post gives background information on the three random words password creation advice.
The author explains how he optimized the performance of conflict-free replicated data types.
Of the 170 registered incidents in 2020, 50 % were caused by system failures, 40 % by human errors, 7 % by natural phenomena, and 2 % by malicious actions.
»Four of the most targeted vulnerabilities in 2020 affected remote work, VPNs, or cloud-based technologies.«
This blog post provides the reader with an in-depth look at eBPF and its security implications in general and details of the specific bug CVE-2021-3490.

»You're crazy if you don't start in the cloud; you're crazy if you stay on it.«