Monthly Shaarli
June, 2021
Virtio-FS is a shared filesystem for letting local virtual machines access host directories.
Besides all the other improvements, SLE 15 SP3 is the first release that provides binary compatibility with the corresponding openSUSE Leap version 15.3.

Google announced »a simple, unified schema for describing vulnerabilities precisely. «
The paper describes Facebook's distributed file system called Tectonic. It can address and store exabytes with optimized resource utilization and less operational complexity.
»Taiwan Semiconductor Manufacturing Co.'s dominance poses risks to the global economy, amid geopolitical tensions and a major chip shortage.«
The author introduces an Ansible playbook for applying best practices for securing Linux servers.
In this study, the authors took a close look into the evolution of UNIX, from the PDP-7 Research Edition to FreeBSD 11.
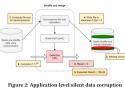
This blog post summarizes the recently published papers of Google and Facebook on the issue of silent data corruption.

Grafana 8.0 was released. Among other improvements, it centralizes alerting information, introduces library panels and real-time streaming.
»ALPACA is an Application layer protocol content confusion attack, exploiting TLS servers implementing different protocols but using compatible certificates, such as multi-domain or wildcard certificates. Attackers can redirect traffic from one subdomain to another, resulting in a valid TLS session.«

The encrypted device company ANOM, developed and operated by the FBI, was used to route messages to an FBI-owned server and decrypted with a master key.
CentOS 8 (2105), based on the Red Hat Enterprise Linux 8.4 source code, was released.
SUSE released openSUSE Leap 15.3. The first release that shares sources and binaries with SUSE Linux Enterprise (SLE) and comes with new features and stability improvements.
Christine Patton, Back End Engineer at SoundCloud, shares best practices for on-call work in this blog post.
»Let's say you're building some form of appliance on top of general purpose x86 hardware. You want to be able to verify the software it's running hasn't been tampered with. What's the best approach with existing technology?«
This article analyzes the different aspects of shells and provides ideas for future improvements.

The article looks at two recent backup issues: One caused by the retention time of iCloud backups and the other caused by the malicious remote factory reset of Western Digital My Book Live NAS, based on a three-year-old CVE that Western Digital never fixed.

Buildah version 1.21.0 introduces the --secret option to pass secret information with it being stored in the final image and will be shipped for Fedora 32, 33, and 34, as well as RHEL 8.5.

» Europe's communication needs are currently almost exclusively delivered by Chinese hardware that connects us to US-based platforms. For a variety of reasons, this is not a good idea.«

Not only are the capabilities of boring technology well understood, but more importantly, their failure modes, too.
Example step-by-step guide for introducing data model changes.
Paper on SeKVM, a modified version of KVM, that guarantees data confidentiality and integrity.
Incident Report on Fastly's service disruption this week.
Animated version control visualization tool.
Drop-in replacement to run your make targets inside a container.
Open Source Insights is an experimental service by Google to better understand the dependencies of open-source software packages. Currently, supported are Cargo (Rust), Go's module system, Maven (Java), and npm (Node.js).
Post on how the integration of password managers into other applications, especially web browsers, increases the attack surface significantly.
EllaLink is a new submarine cable linking the European and South America with a latency <60 ms round-trip delay time between Portugal and Brazil.
Paper by Google on mercurial processor cores that cause computational errors that were not detected during manufacturing tests.

A vCenter pre-auth remote code execution vulnerability with a severity rating of 9.8 out of 10 is under active exploitation.
traitor checks for local misconfigurations and vulnerabilities and exploits them automatically to pop a root shell.
Rocky Linux 8.4, bug-for-bug compatible with Red Hat Enterprise Linux 8.4, is now generally available. The Rocky Linux community also provides a tool to aid the conversation from the 8.4 versions of Alma Linux, CentOS, RHEL, and Oracle Linux.
Debian is moving away from OpenGPG for repository signing.
GitHub Container registry supporting OCI images is now GA and comes with anonymous access for public containers, permission control for containers, and visibility independent of the repository. The existing Docker registry at docker.pkg.github.com will be automatically migrated to the new container registry in the coming weeks.
Debian 10.10 contains the latest corrections for security issues and serious problems.
This article explains how to run docker containers inside QEMU Microvms.
»VPNs are entirely based on trust. «
The authors shed light on metastable failures in distributed systems. Paradoxically, features that improve the efficiency or reliability of the system are often the cause of such errors.
Open-source remote desktop software for Linux.

»Terraform v1.0.0 intentionally has no significant changes compared to Terraform v0.15.5. You can consider the v1.0 series as a direct continuation of the v0.15 series; we do not intend to issue any further releases in the v0.15 series, because all of the v1.0 releases will be only minor updates to address bugs.«

In this 10-minute video, one of the authors summarizes the issues with silent silicon data corruption presented in their »Cores that don't count paper«.
»GNU poke is an interactive, extensible editor for binary data.«
Alibaba's PolarDB extends PostgreSQL to become a share-nothing distributed database.

This article gives insight into the workflows and tools Facebook is using to detect and address PCIe faults.

Version 2.0 of the NVM Express specification has been released.

»By law, users must be given a clear yes/no option. As most banners do not comply with the requirements of the GDPR, noyb developed a software that recognizes various types of unlawful cookie banners and automatically generates complaints.«