Daily Shaarli
June 20, 2021

Buildah version 1.21.0 introduces the --secret option to pass secret information with it being stored in the final image and will be shipped for Fedora 32, 33, and 34, as well as RHEL 8.5.
»VPNs are entirely based on trust. «

» Europe's communication needs are currently almost exclusively delivered by Chinese hardware that connects us to US-based platforms. For a variety of reasons, this is not a good idea.«
In this study, the authors took a close look into the evolution of UNIX, from the PDP-7 Research Edition to FreeBSD 11.
The authors shed light on metastable failures in distributed systems. Paradoxically, features that improve the efficiency or reliability of the system are often the cause of such errors.
The author introduces an Ansible playbook for applying best practices for securing Linux servers.
Debian 10.10 contains the latest corrections for security issues and serious problems.
This article explains how to run docker containers inside QEMU Microvms.
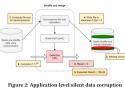
This blog post summarizes the recently published papers of Google and Facebook on the issue of silent data corruption.