According to a source, Ubiquiti's breach in January 2021 was much severe than what the company communicated.
This post explains the issue of DoS against regular expressions. The authors also introduce their tool regexploit, which helps analyze regular expressions against such vulnerabilities.
The author shares his interesting findings in buying and utilizing 14 domains that are 1-bitflip away from windows.com.
This post introduces sigstore, a Linux Foundation project that aims to improve open-source software supply chain integrity and verification.
In this document, Apple explains the different security aspects of its platform.
»The goal of OSV is to provide precise data on where a vulnerability was introduced and where it got fixed, thereby helping consumers of open source software accurately identify if they are impacted and then make security fixes as quickly as possible.«
dog is a command-line DNS client with support for DNS-over-TLS and DNS-over-HTTPS protocols.
This post's authors provide insight into Mozilla's fuzzing-pipeline, including links to the open-source tools in use.
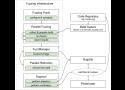
The Threat Modeling Manifesto provides guidelines with values and principles in threat modeling.
»Seven new vulnerabilities are being disclosed in common DNS software dnsmasq, reminiscent of 2008 weaknesses in Internet DNS Architecture.«
The article shows that it's possible to exfiltrate data from air-gapped computers with Wi-Fi signals.
This guide provides extensive information on hardening Linux.
The author illustrates some of the implications of the Virtualization framework in macOS.
»NAT Slipstreaming allows an attacker to remotely access any TCP/UDP service bound to a victim machine, bypassing the victim's NAT/firewall (arbitrary firewall pinhole control), just by the victim visiting a website.«
Security Engineering Book
Terrifying iOS Exploit found in the wild
Impact: The implant has access to almost all of the personal information available on the device, which it is able to upload, unencrypted, to the attacker's server. The implant binary does not persist on the device; if the phone is rebooted then the implant will not run until the device is re-exploited when the user visits a compromised site again. Given the breadth of information stolen, the attackers may nevertheless be able to maintain persistent access to various accounts and services by using the stolen authentication tokens from the keychain, even after they lose access to the device.
Versions of the Official Alpine Linux Docker images (since v3.3) contain a NULL password for the root user.
Halbjahresbericht der Melde- und Analysestelle Informationssicherung
AsiaBSDCon 2019 Keynote.
New attack vector opens backdoor inside enterprise disk storage arrays and people's NAS devices.